DDoS Protection
- Home
- DDoS Protection

Comprehensive DDoS Protection
Our DDoS Protection Services leverage Wanguard technology to provide unparalleled security, filtering up to 100 Gbps in real time and a global protection capacity of over 3 Tbps through our upstream providers.
With our solution, your business benefits from advanced traffic analysis, automated attack detection, and instant response to prevent disruptions, safeguarding your network and ensuring continuous operations.
- 100 Gbps Filtering Capacity
- 3+ Tbps Global Coverage
- Instant Attack Mitigation
- 24/7 NOC Support
How Our DDoS Protection Works
Our solution employs a multi-layered approach, identifying and mitigating threats across network, application, and infrastructure layers.
Detection & Mitigation
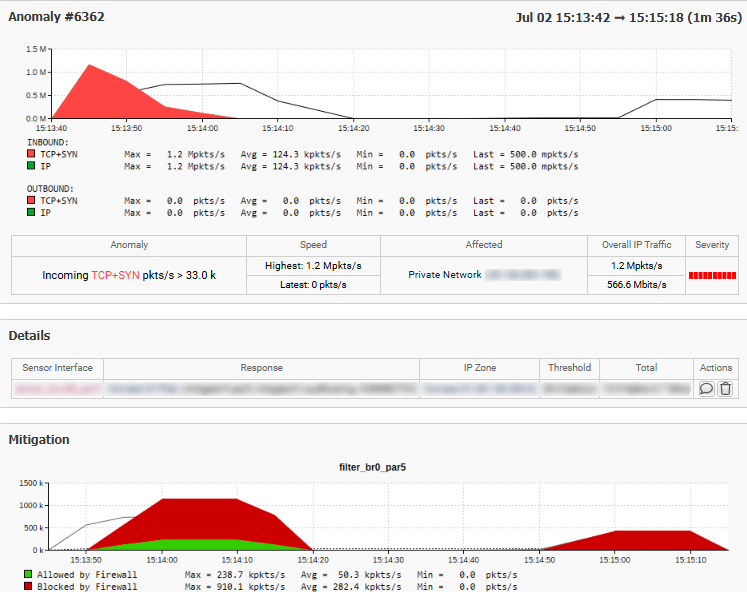
Continuous traffic analysis detects abnormal patterns and proactively addresses potential threats before they impact your operations.
Filter Rules
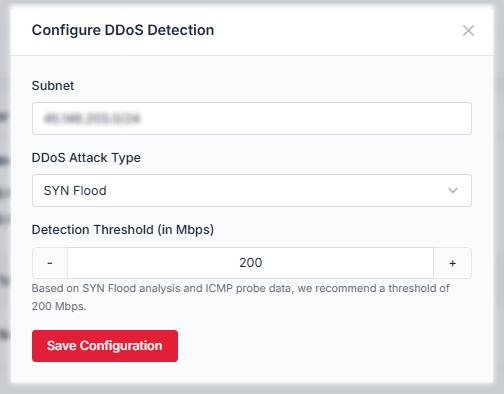
Automated filtering through Wanguard neutralizes attacks instantly, ensuring legitimate traffic reaches your network uninterrupted.
Real-time Analysis
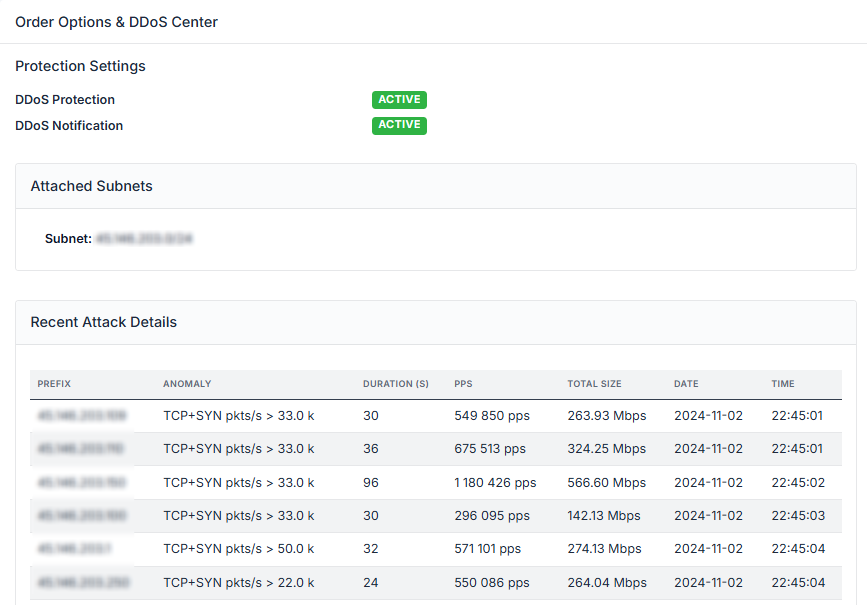
Our tools provide real-time data on network health, enabling quick adjustments to maintain peak performance and resilience.
Image Title
Understanding Different Types of
DDOS ATTACKS
DDoS attacks can vary in complexity and impact. Here is an overview of common attack types and our response strategies:
| Attack Type | Description | Impact | Our Response |
|---|---|---|---|
| Volumetric Attacks | Overwhelms network bandwidth with a flood of traffic. | Severe latency, possible service disruption. | High-capacity filtering, traffic redirection to scrubbing centers. |
| Application Layer Attacks | Targets specific applications, exhausting resources. | Resource exhaustion, application crashes. | Protocol analysis, anomaly detection, adaptive filtering. |
| Protocol Attacks | Exploits protocol vulnerabilities (e.g., SYN floods). | Connection saturation, service unavailability. | Stateful filtering, protocol-level defenses, rate limiting. |
| Multi-Vector Attacks | Combines multiple attack types for maximum impact. | Highly disruptive, difficult to mitigate. | Layered mitigation strategy, comprehensive filtering techniques. |
© CONNECT-IX.NET Register under the number 927 470 765

